
Exploiting Trust: The Abuse of GoDaddy’s CDN for Malware Distribution
Abstract
This research paper explores the exploitation of legitimate content delivery networks (CDNs) by advanced persistent threat (APT) actors to distribute malware. A recent case highlights how GoDaddy’s CDN, supported by Akamai, has been leveraged to spread malicious artifacts through seemingly trusted domains. The findings indicate a significant cybersecurity risk, emphasizing the importance of domain reputation management, sandbox analysis, and proactive mitigation strategies.
Introduction
CDNs play a crucial role in improving web performance and scalability. However, malicious actors have identified vulnerabilities within these infrastructures, enabling them to leverage trusted networks for illicit activities. This study examines the misuse of GoDaddy’s CDN, analyzing its impact, attack vectors, and recommended countermeasures.
Methodology
This research is based on domain analysis using sandbox environments, WHOIS lookups, and threat intelligence reports. Evidence was collected from multiple sources, including JoeSandbox and AlienVault’s Open Threat Exchange (OTX).
Findings
Malware Distribution via GoDaddy CDN
A threat campaign has been identified where malicious scripts were injected into GoDaddy-hosted websites. These scripts exploited GoDaddy’s infrastructure to distribute malware through domains appearing legitimate.
- Sandbox Analysis: A forensic analysis of infected domains (JoeSandbox, 2024) confirmed the presence of malicious scripts embedded within GoDaddy’s CDN.
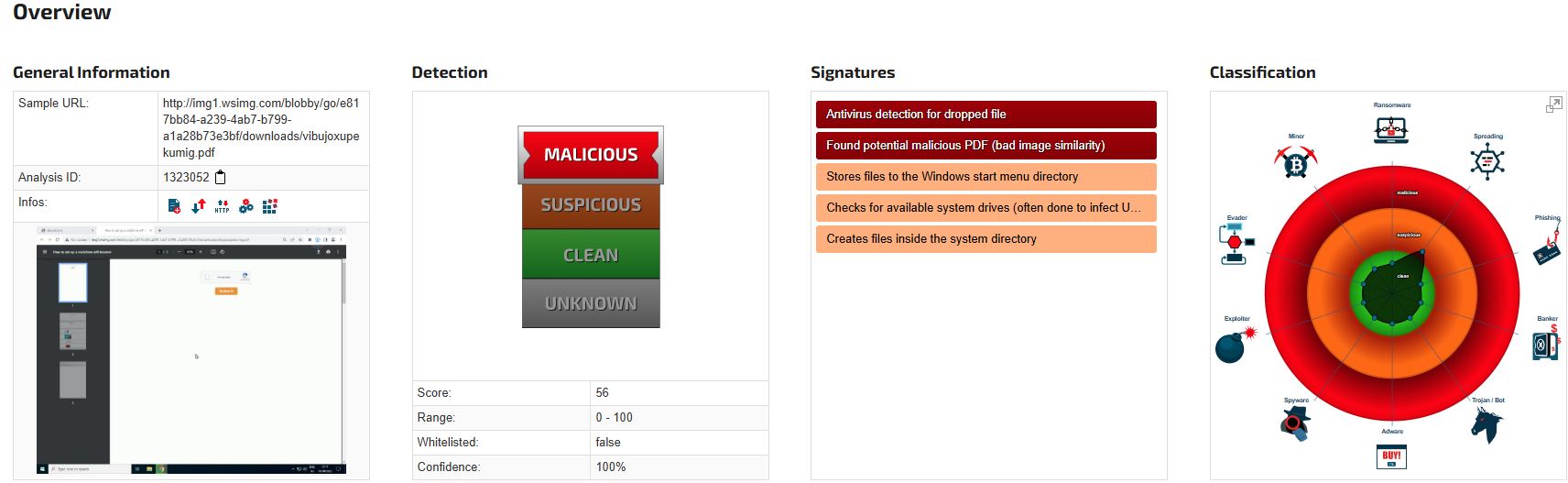
- WHOIS and IP Attribution: The affected domains resolve to IP addresses belonging to Akamai, indicating the involvement of GoDaddy’s caching and content distribution mechanisms (WHOIS, 2024).
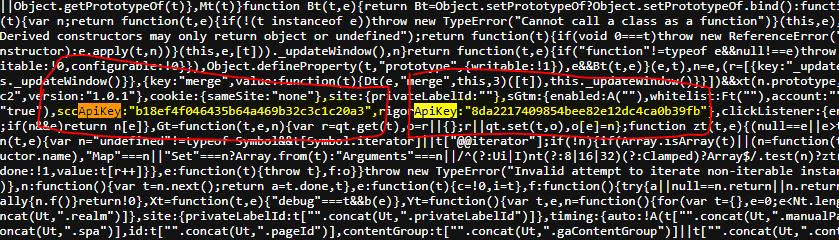
- Exposed API Keys: A critical vulnerability identified in an affected script in many Clients of this provider (GoDaddy) exposed API keys, exacerbating the attack surface and enabling further exploitation.
https://img1.wsimg.com/signals/js/clients/scc-c2/scc-c2.min.js
Discussion
The use of reputable CDNs for malware distribution presents a complex security challenge. Given that security solutions often whitelist such domains, malicious payloads benefit from implicit trust, making detection more difficult. This raises concerns about the need for more stringent monitoring and proactive filtering of third-party scripts injected into hosted environments.
Recommendations
- Disable Third-Party Script Injection: Website owners should revoke consent for automatic script injections by hosting providers to mitigate potential abuse.
- Reevaluate CDN Trust Models: Domains associated with GoDaddy’s CDN should no longer be considered inherently safe; security teams should implement additional validation layers.
- Report and Mitigate: Organizations using GoDaddy should escalate concerns to their hosting provider and monitor for unauthorized changes in their site’s scripts.
- Enhanced Threat Intelligence Sharing: Collaboration between cybersecurity vendors and web service providers can enhance detection and response against such threats.
Conclusion
The exploitation of GoDaddy’s CDN as a malware distribution platform underscores the risks of implicit trust in large-scale content delivery networks. This study highlights the urgency of implementing stronger security measures, both at the infrastructure and individual site levels, to prevent similar attacks in the future.
References
- JoeSandbox Analysis Report: https://www.joesandbox.com/analysis/1323052/0/html
- WHOIS Domain and IP Analysis: https://who.is/whois-ip/ip-address/23.212.249.68, https://who.is/whois-ip/ip-address/23.212.249.79
- AlienVault OTX Indicators: https://otx.alienvault.com/indicator/domain/img1.wsimg.com
- GoDaddy Domain Security Documentation: https://www.godaddy.com/es/help/bloquear-o-desbloquear-mi-dominio-410
This research aims to bring awareness to an emerging threat in cybersecurity and provide actionable intelligence to mitigate the risks associated with compromised CDN infrastructure.
Copyright ©2025 – Hackfluency

